Cybersecurity agency Malwarebytes has warned of a brand new type of crypto-stealing malware hidden inside a “cracked” model of TradingView Premium, software program that gives charting instruments for monetary markets.
The scammers are lurking on crypto subreddits, posting hyperlinks to Home windows and Mac installers for “TradingView Premium Cracked,” which is laced with malware geared toward stealing private information and draining crypto wallets, Jerome Segura, a senior safety researcher at Malwarebytes, said in a March 18 weblog submit.
“Now we have heard of victims whose crypto wallets had been emptied and have been subsequently impersonated by the criminals who despatched phishing hyperlinks to their contacts,” he added.
Fraudsters declare the packages are free and have been cracked straight from their official model, however they're really riddled with malware. Supply: Malwarebytes
As a part of the snare, the fraudsters declare the packages are free and have been cracked straight from their official model, unlocking premium options. It really incorporates two malware packages, Lumma Stealer and Atomic Stealer.
Lumma Stealer is an info stealer that’s been round since 2022 and primarily targets cryptocurrency wallets and two-factor authentication (2FA) browser extensions. Atomic Stealer was first discovered in April 2023 and is understood for its capacity to seize information reminiscent of administrator and keychain passwords.
Moreover “TradingView Premium Cracked,” the scammers have supplied different fraudulent buying and selling packages to focus on crypto merchants on Reddit.
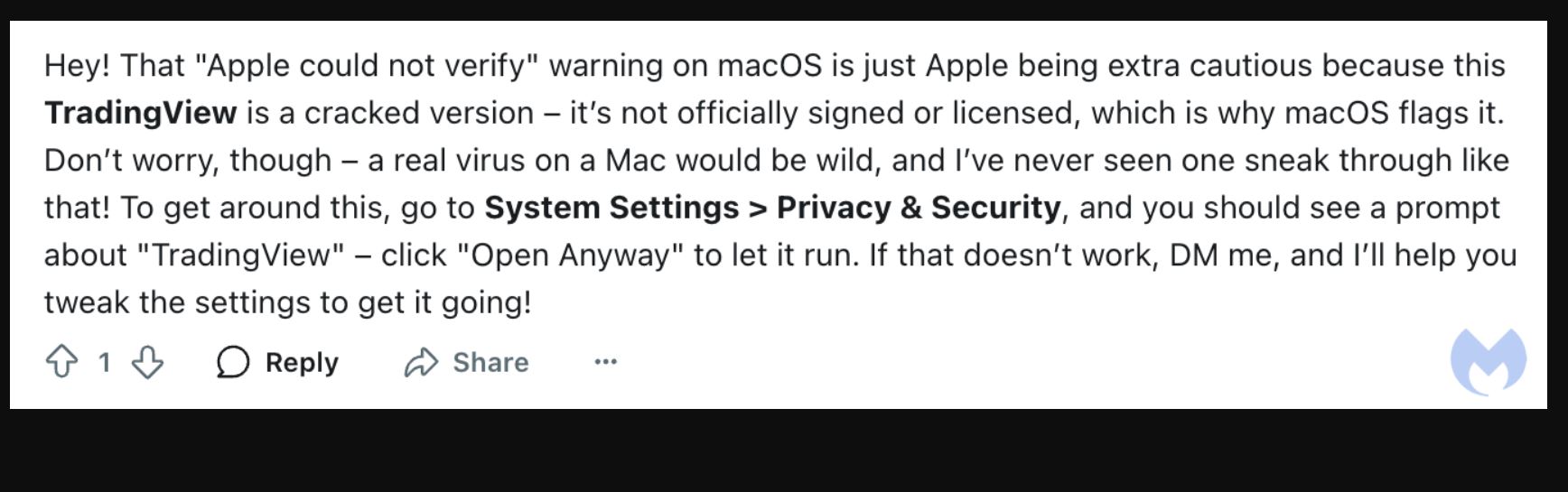
Segura stated one of many fascinating elements of the scheme is that the scammer additionally takes the time to help customers in downloading the malware-ridden software and assist resolve any points with the obtain.
“What’s fascinating with this explicit scheme is how concerned the unique poster is, going by the thread and being ‘useful’ to customers asking questions or reporting a difficulty,” Segura stated.
“Whereas the unique submit provides a heads-up that you're putting in these recordsdata at your personal threat, additional down within the thread, we are able to learn feedback from the Authentic poster.”
On this case, the scammer sticks round to help customers in downloading the malware-ridden software program. Supply: Malwarebytes
The origin of the malware wasn’t clear, however Malwarebytes discovered that the web site internet hosting the recordsdata belonged to a Dubai cleansing firm, and the malware command and management server had been registered by somebody in Russia roughly one week in the past.
Segura says that cracked software program has been vulnerable to containing malware for many years, however the “lure of a free lunch continues to be very interesting.”
Widespread pink flags to be careful for with a majority of these scams are directions to disable safety software program so this system can run and recordsdata which are password-protected, in response to Malwarebytes.
Associated: Microsoft warns of new remote access trojan targeting crypto wallets
On this occasion, Segura says the “recordsdata are double zipped, with the ultimate zip being password protected. For comparability, a reliable executable wouldn't have to be distributed in such trend.”
Blockchain analytics agency Chainalysis reported in its 2025 Crypto Crime Report that crypto crime has entered a professionalized period dominated by AI-driven scams, stablecoin laundering, and environment friendly cyber syndicates. Up to now 12 months, the analytics agency estimates there was $51 billion in illicit transaction quantity.
Journal: Ridiculous ‘Chinese Mint’ crypto scam, Japan dives into stablecoins: Asia Express





