Cybersecurity agency Menace Material says it has discovered a brand new household of mobile-device malware that may launch a faux overlay for sure apps to trick Android customers into offering their crypto seed phrases because it takes over the gadget.
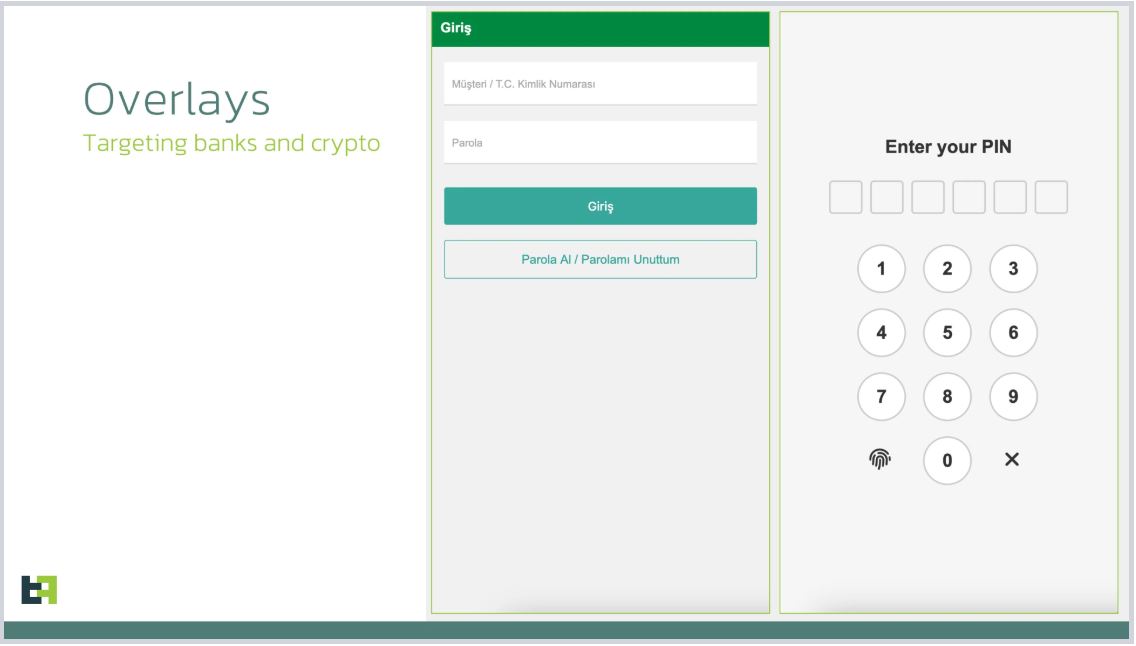
Menace Material analysts said in a March 28 report that the Crocodilus malware makes use of a display screen overlay warning customers to again up their crypto wallet key by a selected deadline or threat dropping entry.
“As soon as a sufferer gives a password from the applying, the overlay will show a message: Again up your pockets key within the settings inside 12 hours. In any other case, the app shall be reset, and it's possible you'll lose entry to your pockets,” Menace Material mentioned.
“This social engineering trick guides the sufferer to navigate to their seed phrase pockets key, permitting Crocodilus to reap the textual content utilizing its accessibility logger.”
Supply: Threat Fabric
As soon as the risk actors have the seed phrase, they'll seize full management of the pockets and “drain it fully.”
Menace Material says regardless of it being a brand new malware, Crocodilus has all of the options of recent banking malware, with overlay assaults, superior information harvesting by way of display screen seize of delicate data corresponding to passwords and distant entry to take management of the contaminated gadget.
Preliminary an infection happens by inadvertently downloading the malware in different software program that bypasses Android 13 and safety protections, based on Menace Material.
As soon as put in, Crocodilus requests accessibility service to be enabled, which permits the hackers to realize entry to the gadget.
“As soon as granted, the malware connects to the command-and-control (C2) server to obtain directions, together with the listing of goal functions and the overlays for use,” Menace Material mentioned.
As soon as put in, Crocodilus requests accessibility service to be enabled, granting hackers entry to the gadget. Supply: Threat Fabric
It runs repeatedly, monitoring app launches and displaying overlays to intercept credentials. When a focused banking or cryptocurrency app is opened, the faux overlay launches excessive and mutes the sound whereas the hackers take management of the gadget.
“With stolen PII and credentials, risk actors can take full management of a sufferer’s gadget utilizing built-in distant entry, finishing fraudulent transactions with out detection,” Menace Material mentioned.
Menace Fabrix’s Cellular Menace Intelligence workforce has discovered the malware targets users in Turkey and Spain however mentioned the scope of use will doubtless broaden over time.
Associated: Beware of ‘cracked’ TradingView — it’s a crypto-stealing trojan
Additionally they speculate the builders might communicate Turkish, primarily based on the notes within the code, and added {that a} risk actor often called Sybra or another hacker testing out new software program may very well be behind the malware.
“The emergence of the Crocodilus cellular banking Trojan marks a big escalation within the sophistication and risk degree posed by trendy malware.”
“With its superior Machine-Takeover capabilities, distant management options, and the deployment of black overlay assaults from its earliest iterations, Crocodilus demonstrates a degree of maturity unusual in newly found threats,” Menace Material added.
Journal: Ridiculous ‘Chinese Mint’ crypto scam, Japan dives into stablecoins: Asia Express





