A minimum of three crypto founders have reported foiling an try from alleged North Korean hackers to steal delicate knowledge by means of pretend Zoom calls over the previous few days.
Nick Bax, a member of the white hat hacker group the Safety Alliance, mentioned in a March 11 X post the tactic utilized by North Korean scammers had seen tens of millions of {dollars} stolen from suspecting victims.
Usually, the scammers will contact a goal with a gathering provide or partnership, however as soon as the decision begins, they ship a message feigning audio points whereas a inventory video of a bored enterprise capitalist is on the display; they then ship a hyperlink to a brand new name, in accordance with Bax.
Having audio points in your Zoom name? That is not a VC, it is North Korean hackers.
Luckily, this founder realized what was happening.
The decision begins with just a few "VCs" on the decision. They ship messages within the chat saying they cannot hear your audio, or suggesting there's an… pic.twitter.com/ZnW8Mtof4F
— Nick Bax.eth (@bax1337) March 11, 2025
“It’s a pretend hyperlink and instructs the goal to put in a patch to repair their audio/video,” Bax mentioned.
“They exploit human psychology, you assume you’re assembly with necessary VCs and rush to repair the audio, inflicting you to be much less cautious than you often are. As soon as you put in the patch, you’re rekt.”
The submit prompted a number of crypto founders to element their experiences with the rip-off.
Giulio Xiloyannis, co-founder of the blockchain gaming Mon Protocol, said scammers tried to dupe him and the top of promoting with a gathering a few partnership alternative.
Nonetheless, he was alerted to the ruse when, on the final minute, he was prompted to make use of a Zoom hyperlink that “pretends to not be capable to learn your audio to make you put in malware.”
“The second I noticed a Gumicryptos accomplice talking and a Superstate one I noticed one thing was off,” he mentioned.
Supply: Giulio Xiloyannis
David Zhang, co-founder of US venture-backed stablecoin Stably, was additionally focused. He said the scammers used his Google Meet hyperlink however then made up an excuse about an inner assembly, asking him to hitch that assembly as an alternative.
“The location acted like a traditional Zoom name. I took the decision on my pill although, so unsure what the habits would’ve been on desktop,” Zhang mentioned.
“It in all probability tried to find out the OS earlier than prompting the consumer to do one thing, nevertheless it simply wasn’t constructed for cellular Oses.”
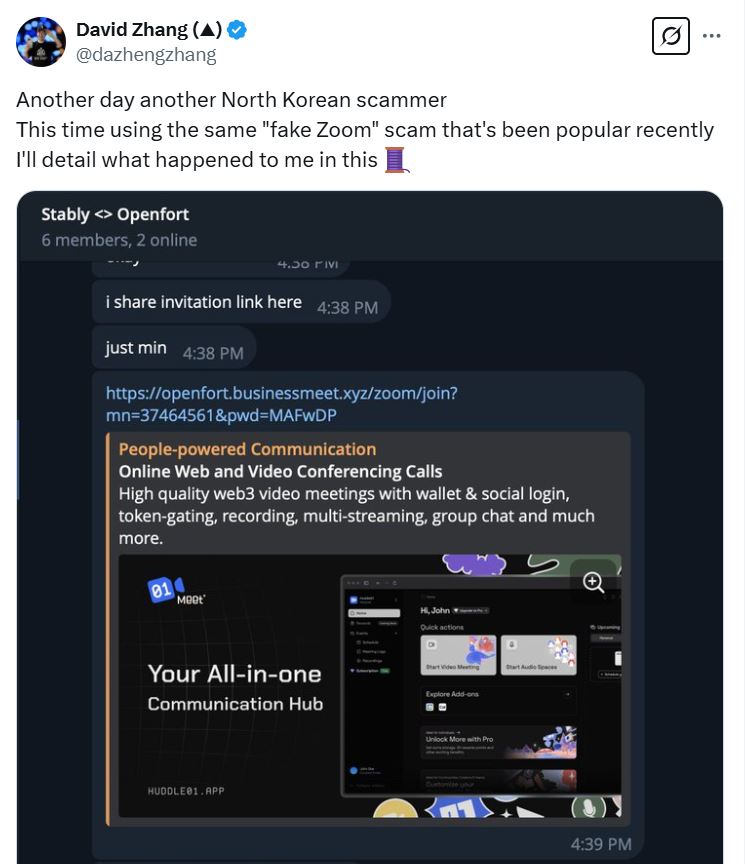
Supply: David Zhang
Melbin Thomas, founding father of Devdock AI, a decentralized AI platform for Web3 tasks, said he was additionally hit with the rip-off and was not sure if his tech was nonetheless in danger.
“The identical factor occurred to me. However I didn’t give my password whereas the set up was taking place,” he mentioned.
“Disconnected my laptop computer and I reset to manufacturing unit settings. However transferred my recordsdata to a tough drive. I've not linked the laborious drive again to my laptop computer. Is it nonetheless contaminated?”
Associated: Fake Zoom malware steals crypto while it’s ‘stuck’ loading, user warns
This comes after the US, Japan and South Korea on Jan. 14 issued a joint warning against the growing threat introduced by cryptocurrency hackers related to North Korean hackers.
Teams such because the Lazarus Group are prime suspects in a few of the largest cyber thefts in Web3, together with the Bybit $1.4 billion hack and the $600 million Ronin network hack.
The Lazarus Group has been shifting crypto property utilizing mixers following a string of high-profile hacks, according to blockchain security firm CertiK, which detected a deposit of 400 Ether (ETH) price round $750,000 to the Twister Money mixing service.
Journal: Lazarus Group’s favorite exploit revealed — Crypto hacks analysis





