[ad_1]
Understanding open-source protocols
Open-source protocols have turn into a mainstay within the tech world and are gaining traction because of the myriad advantages that they provide over their proprietary counterparts.
The protocols are usually created with the intention of being utilized by the general public, enabling anybody to look at, alter and share their code. The advantages of open-source protocols are multifaceted, starting from their inherent transparency to their wider accessibility.
Moreover, they depend on peer evaluations, a cheap and inclusive mannequin that distinguishes them from their proprietary counterparts. Distinguished examples of open-source software program embody extensively used operating systems resembling Linux and Android and the favored Firefox internet browser.
In the case of open-source cryptographic protocols, the Bitcoin, Ethereum, Cardano and Polkadot networks stand out as noteworthy blockchain protocol exemplars, amongst others.
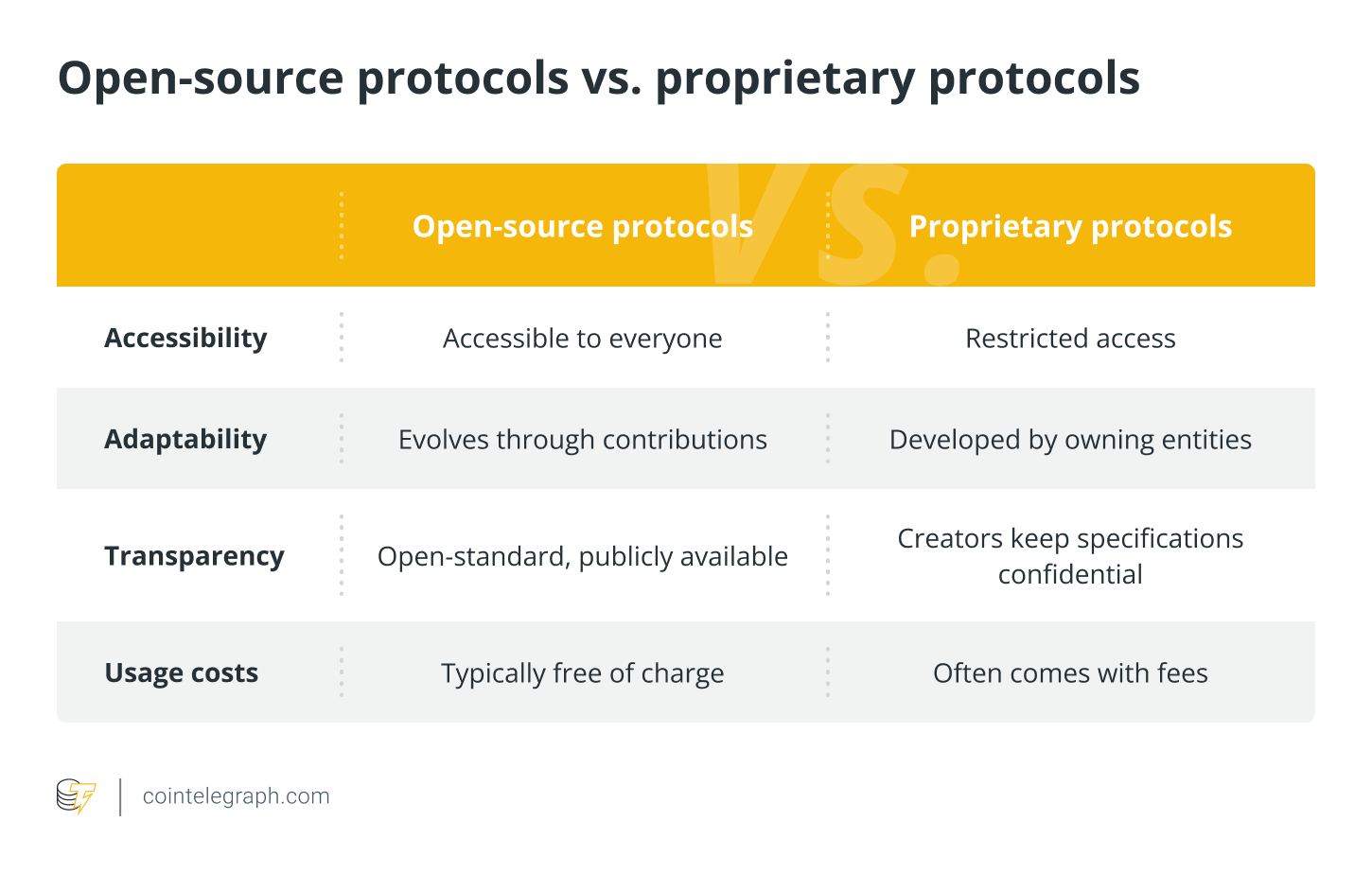
Open-source vs. proprietary protocols
Open-source and proprietary protocols signify two distinct approaches to protocol growth, every with its personal set of ideas on the subject of protocol implementation.
The next is a dissection of their key disparities:
What’s the event course of for open-source protocols?
The event of open-source protocols includes a number of distinct phases, every integral to a protocol’s evolution. All of it begins with the conceptualization part, the place builders lay the inspiration that defines the protocol’s requirements and function.
Normally, the fundamental idea relies on an current protocol with some enhancements. The conceptualization stage acts because the bedrock, upon which builders meticulously define the structure and options, forming a sturdy theoretical basis. On this part, builders chart out a well-defined roadmap, akin to a strategic plan, guiding the challenge’s trajectory.
The next step within the growth course of is normally the prototyping stage. On this stage, builders create a practical mannequin of the protocol that features the important thing proposed options. The prototype is normally made accessible to the general public because the beta model.
Releasing the beta model topics the software program to real-world eventualities and person interactions, permitting builders to discern its strengths and weaknesses. The stage additionally permits builders to get suggestions from the open-source neighborhood relating to potential new options to include earlier than the ultimate protocol is launched. Due to this fact, the stage is aptly known as the beta testing or person acceptance testing (UAT) stage.
Steady suggestions and updating be certain that the protocol stays aware of the evolving wants and expectations of its person base. After related protocol upgrades are applied to resolve most of the identified stability and reliability points, the protocol reaches a degree of stability warranting the designation of a “steady launch.” The steady launch model is normally as dependable as builders could make it.
Nevertheless, the method doesn’t culminate in steady releases. Open-source tasks require ongoing protocol upkeep. The method normally entails releasing bug fixes, resembling safety patches, and updating the code for enhanced compatibility.
Are open-source protocols copyrighted?
When a developer publishes their code as open-source, they’re sharing it with the general public, permitting others to make use of, modify and distribute it. Nevertheless, the act of creating the code public doesn’t translate to unrestricted utilization.
Copyright legal guidelines apply right here, simply as they do for proprietary software program. The legal guidelines routinely safeguard any unique inventive work, together with open-source protocols, granting the software program creator unique rights to manage their use and distribution.
In the case of open-source protocol licensing, the developer usually attaches a license to it, which acts as a set of tips that clearly delineates what’s permissible and what’s off-limits regarding the code.
Open-source licenses usually grant customers intensive permissions without having specific approval from the unique creator. That mentioned, there are two foremost kinds of open-source licenses: permissive and copyleft.
A permissive license, typically additionally referred to as a BSD-style or Apache-style license, imposes minimal necessities on how the software program may be modified or redistributed. Nevertheless, tasks that use this sort of license are obliged to append a guaranty disclaimer. A traditional instance of a permissive license is the MIT License. The license permits anybody to make use of, modify and distribute the code with out prior consent.
Initiatives using MIT-licensed code usually should incorporate the unique copyright discover and a disclaimer explicitly stating that the software program comes with none guarantee. The disclaimer clarifies that the copyright holders bear no duty for any claims or liabilities stemming from the software program’s use.
The license is exceedingly permissive and is crafted to supply most freedom to builders, even allowing the code’s inclusion and distribution in industrial merchandise.
Relating to copyleft licenses, tasks that use them are additionally required to affix a legal responsibility disclaimer. They arrive with extra restrictions, particularly regarding the distribution of modified protocol variations. For example, the copyleft GNU Common Public License (GPL), a extensively employed open-source license, ensures that the software program stays open and free. Just like the MIT License, the GPL mandates a guaranty disclaimer.
Copyleft licenses assure that open-source protocols or software program may be utilized, tweaked and shared with out constraints. Nevertheless, any modified work should adhere to the identical phrases, preserving the protocol’s openness in all future variations.
In the case of proprietary protocols, the panorama adjustments dramatically. The protocols impose stringent limitations on their protocol documentation, which frequently embody restrictions on modifying or reverse-engineering the code.
To uphold protocol safety, proprietary tasks normally embody confidentiality clauses of their licenses, stopping customers from disclosing their protocols’ workings or any proprietary data they could come throughout.
When it comes to value, permissive and copyleft licenses are free, permitting customers to make use of and distribute the software program with out cost. In distinction, proprietary licenses usually require customers to pay for entry to and use of the software program.
The way forward for open-source protocols
Because the world turns into more and more digital and interconnected, open-source protocols are poised to play a key position in enabling innovation, particularly on the subject of supporting interoperability amongst completely different methods, purposes and gadgets.
The shift is pushed by the widespread, concurrent utilization of protocols crafted by completely different builders on an on a regular basis foundation. In consequence, open-source protocols, particularly those who enable alterations by third events and help interoperable methods, are sure to take middle stage within the new technological frontier.
Going by present traits, open-source tasks are additionally more likely to give attention to sustainability, power effectivity and problem-solving in alignment with the worldwide push for eco-friendly technological options.
Moreover, open-source networking protocol initiatives are anticipated to proceed creating peer-to-peer (P2P) web protocols. The protocols facilitate direct communication between methods, eliminating the necessity for centralized middleman methods. P2P protocols boast an increasing array of purposes, notably in enabling P2P transactions and communications via decentralized protocols.
[ad_2]
Source link





